Information Technology/Operational Technology (IT/OT) Security Convergence in the Smart Building Technology Market, Forecast to 2022
Information Technology/Operational Technology (IT/OT) Security Convergence in the Smart Building Technology Market, Forecast to 2022
Digitalization and Cyberattacks driving adoption of IT/OT Security in Smart Buildings
30-Jul-2019
Europe
Description
Automation, IoT, and digitalization are rapidly changing, and enterprise operations and building operations have not made an exception either. Today, smart devices control building management activities including temperature control, access control, lighting control, communication, and safety systems in many enterprises. At the same time, such converged Information Technology/Operational Technology (IT/OT) environment has made enterprises more vulnerable to cyberattacks. With diverse protocols, hardware, and software systems, the OT devices controlling building operations provide a heterogeneous environment. Coupled with IT devices and a common network connection, the attack surface expands, providing a thriving ground for cyberadversaries to play on.
This study explores the impact of such IT/OT convergence in smart buildings on the cyber posture of an enterprise. The study provides detailed insights on key market trends, risk posture, market dynamics, and vendor dynamics in this market.
Research Scope
Geographical Analysis:
- Europe, the Middle East, and Africa
- Asia-Pacific
- North America and Latin America
The base year for the study is 2018 and the forecast period is from 2019 to 2022.
Insights included:
- Market Dynamics
- Market Trends
- IT/OT Security Risk Matrix Across Verticals and Regions
- Competitor Analysis and Key Vendor Profiles
- Insights for CISOs
- Growth Opportunities
Research Highlights
The IT/OT security market for smart buildings is in its early growth stage, contributing to a small percentage of Industrial Cybersecurity Systems (ICS) security vendors. Growing frequency of cyberattacks exploiting gaps in building OT devices is driving remarkable increase in adoption of IT/OT security among enterprises. However, security budget constraint continues to be a significant challenge for growth. Verticals such as healthcare, hospitality, finance, and data centers promise high growth opportunities for vendors in this market owing to the high cost of impact of cyberattacks in these verticals. Technological capabilities, scalability, and interoperability are key factors of differentiation among vendors operating in the IT/OT security market.
Author: Swetha Ramachandran Krishnamoorthi
RESEARCH: INFOGRAPHIC
This infographic presents a brief overview of the research, and highlights the key topics discussed in it.Click image to view it in full size
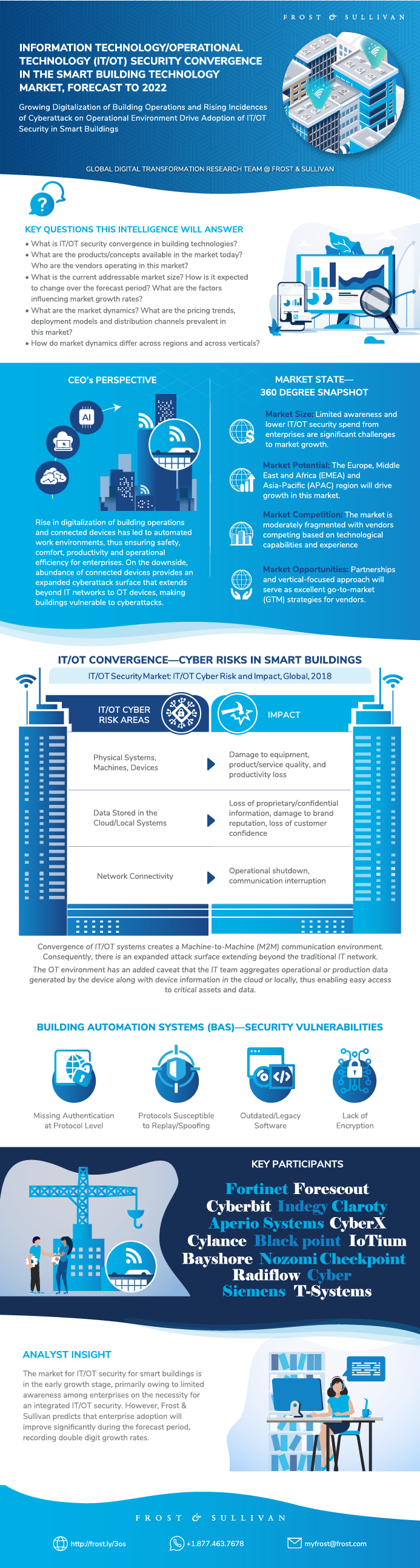
Table of Contents
Key Findings
Market State—360 Degree Snapshot
Research Scope
Research Scope (continued)
Key Questions this Study will Answer
Market Definitions
Geographical Segmentation
Internet of Things (IoT) Penetration
IoT Penetration by Region
Smart Building Control Devices—Commercial
Smart Building Control Devices—Commercial (continued)
IT/OT Convergence
IT/OT Convergence—Merits Versus Risks
Notable IT/OT Cyberattacks
IT/OT Convergence—Cyber Risks in Smart Buildings
BAS
BAS—Security Vulnerabilities
IT/OT Security—Entry Points
IT/OT Security Ecosystem—Types of Stakeholders
Distribution Channels
Distribution Channels—Discussion
Business Models
Regulations and Standards
Market Impact of Growth Trends
Digitization of Building Operations
IT/OT Cybersecurity Spend
IT/OT Security Implementation Challenges
Technology (Mis)Alignment
Forecast Assumptions
Risks to Frost & Sullivan Market Forecasts
Revenue Forecast
Revenue Forecast Discussion
Percent Revenue Forecast by Business Size
Percent Revenue Forecast Discussion by Business Size
Percent Revenue Forecast by Region
Revenue Forecast by Region
Revenue Forecast Discussion by Region
Percent Revenue Forecast by Verticals
Revenue Forecast by Verticals
Revenue Forecast Discussion by Verticals
IT/OT Security Risk Matrix
IT/OT Security Risk Matrix by Verticals
IT/OT Security Risk Matrix Discussion by Verticals
IT/OT Security Risk Matrix by Country/Region
IT/OT Security Risk Matrix Discussion by Country/Region
Competitive Environment
Key Competitor Profile—Aperio Systems (Aperio)
Key Competitor Profile—Aperio Systems (Aperio) (continued)
Key Competitor Profile—Bayshore Networks (Bayshore)
Key Competitor Profile—Bayshore Networks (Bayshore) (continued)
Key Competitor Profile—Check Point Software Technologies (Check Point)
Key Competitor Profile—Check Point Software Technologies (Check Point) (continued)
Key Competitor Profile—Claroty
Key Competitor Profile—Claroty (continued)
Key Competitor Profile—Cyberbit
Key Competitor Profile—Cyberbit (continued)
Key Competitor Profile—Forescout Technologies (Forescout)
Key Competitor Profile—Forescout Technologies (Forescout) (continued)
Key Competitor Profile—Fortinet
Key Competitor Profile—Fortinet (continued)
Key Competitor Profile—Indegy
Key Competitor Profile—Indegy (continued)
Key Competitor Profile—Iotium
Key Competitor Profile—Iotium (continued)
Key Competitor Profile—Radiflow
Key Competitor Profile—Radiflow (continued)
Key Competitor Profile—Siemens Smart Infrastructure
Key Competitor Profile—Siemens Smart Infrastructure (continued)
Key Competitor Profile—Siemens Smart Infrastructure (continued)
Key Competitor Profile—T-Systems Telekom Security (T-Systems)
Key Competitor Profile—T-Systems Telekom Security (T-Systems) (continued)
Implementation Steps
Step 1—Asset Inventory
Step 2—Vulnerability, Risk, and Impact Assessment
Step 3—Stakeholder Responsibility
Step 4—Vendor Selection
Step 5—Continued Audit and Improvement
Frost & Sullivan Cyber Resilience Model
Common Mistakes to Avoid
Growth Opportunity 1—Deep Learning and AI
Growth Opportunity 2—Partnerships
Growth Opportunity 3—Vertical Focus
Growth Opportunity 4—Threat Protection
Strategic Imperatives for Success and Growth
The Last Word
Legal Disclaimer
Partial List of Companies Interviewed
Learn More—Next Steps
List of Exhibits
List of Exhibits (continued)
The Frost & Sullivan Story
Value Proposition—Future of Your Company & Career
Global Perspective
Industry Convergence
360º Research Perspective
Implementation Excellence
Our Blue Ocean Strategy
Popular Topics
Research Scope
Geographical Analysis:
- Europe, the Middle East, and Africa
- Asia-Pacific
- North America and Latin America
The base year for the study is 2018 and the forecast period is from 2019 to 2022.
Insights included:
- Market Dynamics
- Market Trends
- IT/OT Security Risk Matrix Across Verticals and Regions
- Competitor Analysis and Key Vendor Profiles
- Insights for CISOs
- Growth Opportunities
Research Highlights
The IT/OT security market for smart buildings is in its early growth stage, contributing to a small percentage of Industrial Cybersecurity Systems (ICS) security vendors. Growing frequency of cyberattacks exploiting gaps in building OT devices is driving remarkable increase in adoption of IT/OT security among enterprises. However, security budget constraint continues to be a significant challenge for growth. Verticals such as healthcare, hospitality, finance, and data centers promise high growth opportunities for vendors in this market owing to the high cost of impact of cyberattacks in these verticals. Technological capabilities, scalability, and interoperability are key factors of differentiation among vendors operating in the IT/OT security market.
Author: Swetha Ramachandran Krishnamoorthi
| No Index | No |
|---|---|
| Podcast | No |
| Author | Swetha Ramachandran Krishnamoorthi |
| Industries | Information Technology |
| WIP Number | ME8F-01-00-00-00 |
| Is Prebook | No |
| GPS Codes | 9705-C1,9AA6-C1,9659,9B07-C1 |
 USD
USD GBP
GBP CNY
CNY EUR
EUR INR
INR JPY
JPY MYR
MYR ZAR
ZAR KRW
KRW THB
THB