Asia-Pacific Industrial Internet of Things Security, 2018
Asia-Pacific Industrial Internet of Things Security, 2018
The Need for Cybersecurity Among Industrial Firms is Growing
29-Mar-2019
Asia Pacific
$3,000.00
Special Price $2,250.00 save 25 %
Description
In an industrial set-up, various equipment's and components such as controllers, servers, remote terminals, monitoring equipment, and sensors are connected to the internet. Further, computer systems, applications, moving assets to the cloud or even remote facilities being connected to the Wide Area Network (WAN) require internet usage. All these are being done to gather real time insights for enhanced decision making.
However, this is increasing the attack surface. Adding several IoT devices to the network is only creating challenges for managing security as they may transmit sensitive data. Further, with the IT-OT convergence, the attack surface is expanding and subject to higher risks. IT personnel are still focusing on the security of IT network with little insight on securing the OT infrastructure. They are still focused on legacy applications that are difficult to upgrade. They also have limited opportunities for patch management due to the growing number of vulnerabilities. Further, IoT devices are under attack for various reasons such a poor installation of different codes and devices and lack of security experts in IoT security.
To meet the growing challenges of attacks, various vendors are providing security solutions across the IIoT architecture and not just for IT/OT networks, to ensure security against every potential threat.
Traditionally, most IoT devices were made by engineers who had limited knowledge of cyber security, and the devices often had no built-in security. However, with the growing cyber-attacks on industrial firms, cyber security firms are focusing on ‘Security by Design’ by incorporating features such as password protection, multi-factor authentication, and other stronger security capabilities.
While every industrial firm has it’s own unique environment, protecting the organization from IoT related cyber threats is gaining even more significance than ever. These IoT devices and applications can leak out sensitive information that can have a major impact on the organization. As with unprotected IoT applications, the embedded programs can be analysed and stolen, an organization should only think of protecting them and ensure cyber security for their environment.
As more and more industrial firms adopt IIoT, smart technology and automation, their chances of witnessing a security incident rises. Today, as these industrial firms look at optimizing business operations, reduce operating costs, increase control over distributed operations and face an increasing compliance requirement with regulations, they cannot stay away from adopting IIoT.
IIoT and Industry 4.0 are driving organizations looking to improve existing processes and augment operational systems, to facilitate more connections between the physical process world and the Internet. This connectivity exposes the previously isolated operational environments to cyber threats.
Author: Divya Prasad
RESEARCH: INFOGRAPHIC
This infographic presents a brief overview of the research, and highlights the key topics discussed in it.Click image to view it in full size
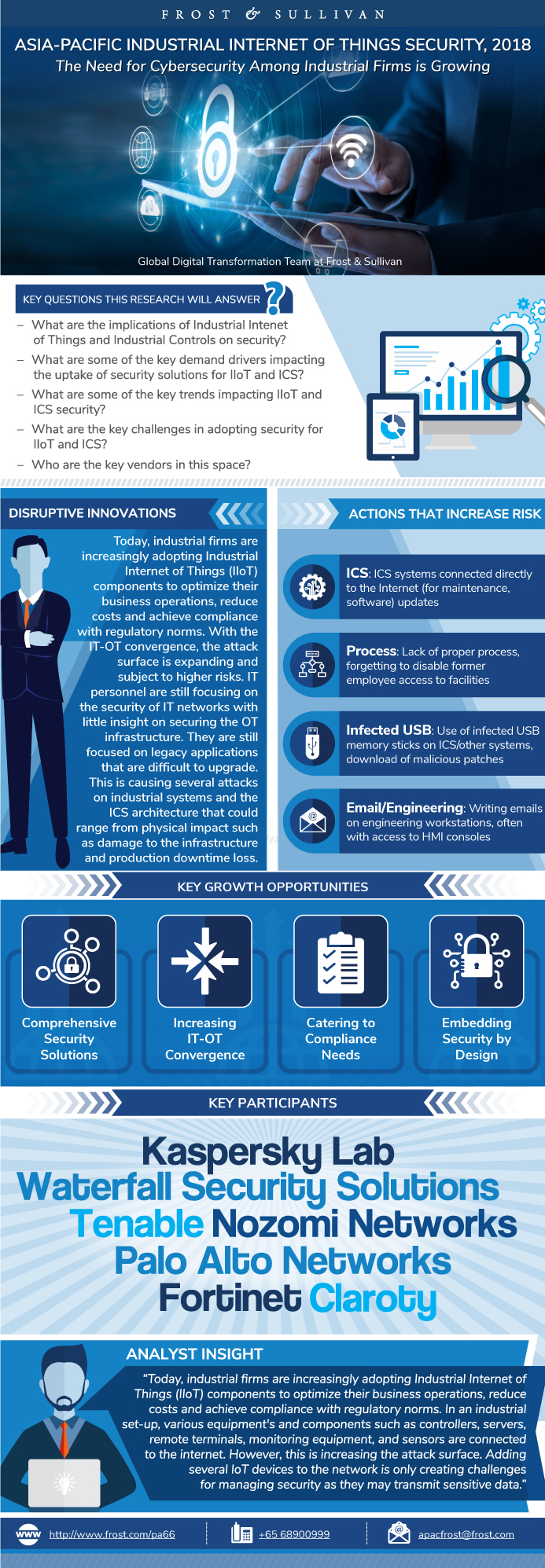
Table of Contents
Executive Summary
Executive Summary (continued)
Understanding Cybersecurity Implications in an IIoT and ICS Environment
Recent Major Attacks
Actions that Increase Risk
Increasing Demand for Cybersecurity Solutions
Higher Demand for Security Solutions
New Threats to Legacy Systems
The Fading of the Air Gap Principle
The Fading of the Air Gap Principle (continued)
Stringent Government Regulations
Key Trends that Affect the Uptake of IIoT Security Solutions
Security Solutions that Cover the Entire IIoT Architecture
The Focus on ‘Security by Design’
The Emergence of Vendors with Advanced IIoT Security Solutions
The Lag in the Adoption of IIoT Security
Lack of Awareness Among OT Professionals
Deploying IIoT Applications Across Industries and the Emerging Security Issues
Case Study—Pavlodar Oil Refinery
Case Study—Murrumbidgee
Case Study—Enel
Growth Opportunity 1—The Demand for Comprehensive Security Solutions from Industrial Firms
Growth Opportunity 2—Increasing Collaboration on Security Strategies Between IT and OT Teams
Growth Opportunity 3—Higher Risk in an Industrial Set-up
Growth Opportunity 4—Adopting ‘Security by Design’ to Ensure Higher Security
4 Major Growth Opportunities
Strategic Imperatives for Success and Growth
Key Vendor Profiles
Vendor Competitive Overview
Claroty
Claroty’s Support for Multiple Teams and Use Cases
Fortinet
Fortinet ICS/SCADA Solution Components
Kaspersky Lab
Kaspersky Lab (continued)
Portfolio of Products and Services Under KICS
Nozomi Networks
Nozomi Networks Solution Architecture
Palo Alto Networks
Palo Alto Networks’ Security Operating Platform Approach for IoT
Tenable
Tenable (continued)
Waterfall Security Solutions
Waterfall Security Solutions—Unidirectional CloudConnect
A Final Word
Legal Disclaimer
The Frost & Sullivan Story
Value Proposition—Future of Your Company & Career
Global Perspective
Industry Convergence
360º Research Perspective
Implementation Excellence
Our Blue Ocean Strategy
| No Index | No |
|---|---|
| Podcast | No |
| Author | Divya Prasad |
| Industries | Information Technology |
| WIP Number | PA66-01-00-00-00 |
| Is Prebook | No |
| GPS Codes | 9532-C1,9702-C1,9705-C1,9658,9659,9887-C1,9B07-C1 |
 USD
USD GBP
GBP CNY
CNY EUR
EUR INR
INR JPY
JPY MYR
MYR ZAR
ZAR KRW
KRW THB
THB