Global Privileged Access Management (PAM) Solutions Growth Opportunities
Global Privileged Access Management (PAM) Solutions Growth Opportunities Updated Research Available
The Ever-changing Threat Landscape and Expanded Attack Surface Drive the Future Growth Potential of Privileged Access Management Solutions
21-Dec-2021
North America
Description
Cyberattacks continued to increase in 2020 and will constantly evolve in the future with increasing sophistication and blended techniques. Attacks on privileged accounts are expected to rise, as working from home and hybrid working environments will continue to prevail in the years to come due to the pandemic.
The digital transformation journey creates a greater attack surface for businesses, as companies tend to use different technologies and applications to facilitate the transformation process. The surge in adoption of applications and machines for daily business operations that require privileged access to the corporate’s services and database to perform their routine tasks are the weak points in the enterprise’s security architecture, as they can be vulnerable to cyberattacks. For example, the use of Robotic Process Automation (RPA), business workload automation, and Industrial Internet of Things (IIoT) is creating a huge number of non-human identities with privileged access, which eventually expands the attack surface.
Thus, it is paramount that organizations have full visibility and control of their applications and machines to address issues related to privileged access. By implementing intelligent and automated PAM solutions, organizations are able to strengthen their security management over privileged accounts and access to reduce attack surfaces. PAM will help them effectively monitor and manage all privileged accounts and access to critical assets at every layer in the organization. PAM also enables businesses to achieve the least privilege principle by easily setting out zero-trust policies to all privileged accounts, normal accounts, applications, and endpoints, which will help detect high-risk activities and enable organizations to enhance their overall cybersecurity posture.
Author: Vivien Pua
RESEARCH: INFOGRAPHIC
This infographic presents a brief overview of the research, and highlights the key topics discussed in it.Click image to view it in full size
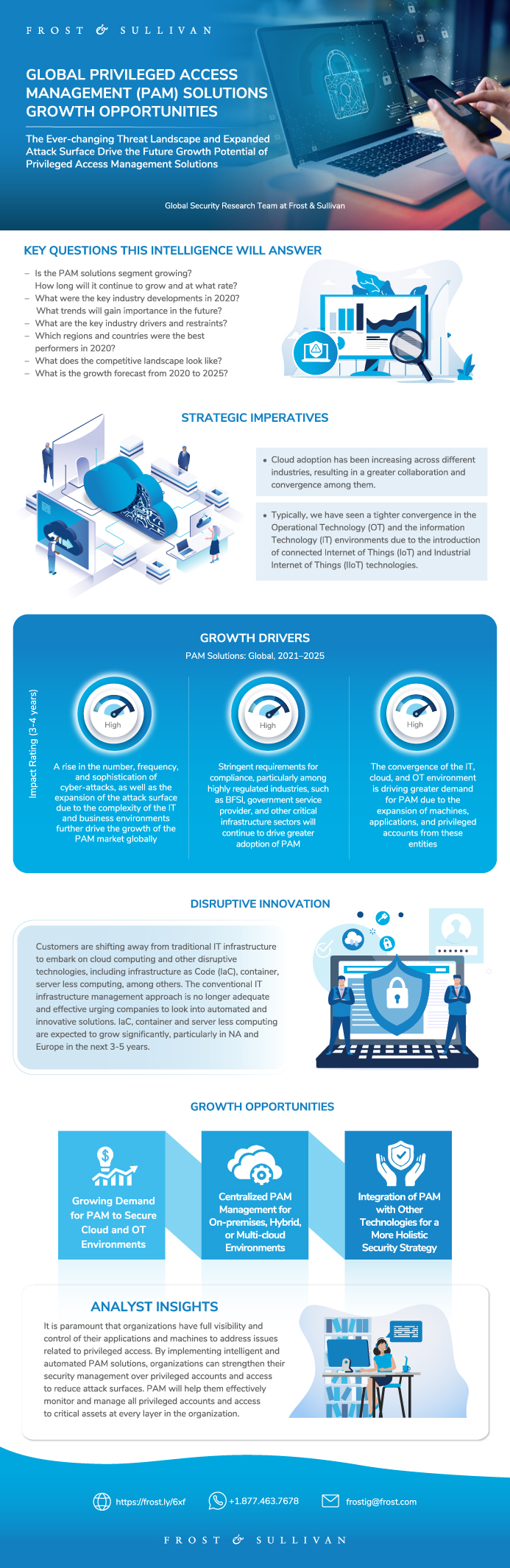
Table of Contents
Why is it Increasingly Difficult to Grow?
The Strategic Imperative 8™
The Impact of the Top Three Strategic Imperatives on Global PAM Industry
Growth Opportunities Fuel the Growth Pipeline Engine™
Global PAM Solutions—Scope of Analysis
Market Definitions
Market Definitions (continued)
Market Definitions (continued)
Customer Segmentation
Research Methodology
Global PAM Solutions—Regional Segmentation
Key Global PAM Solutions Competitors
Key Global PAM Solutions Competitors (continued)
Key Growth Metrics for Global PAM Solutions
Growth Drivers for Global PAM Solutions
Growth Driver Analysis for Global PAM Solutions
Growth Driver Analysis for Global PAM Solutions (continued)
Growth Driver Analysis for Global PAM Solutions (continued)
Growth Driver Analysis for Global PAM Solutions (continued)
Growth Restraints for Global PAM Solutions
Growth Restraint Analysis for Global PAM Solutions
Growth Restraint Analysis for Global PAM Solutions (continued)
Forecast Assumptions—Global PAM Solutions
Forecast Assumptions—Global PAM Solutions (continued)
Revenue Forecast—Global PAM Solutions
Revenue Forecast by Product—Global PAM Solutions
Revenue Forecast by Region—Global PAM Solutions
Revenue Forecast Analysis—Global PAM Solutions
Revenue Forecast Analysis by Region—Global PAM Solutions
Pricing Trends and Forecast Analysis—Global PAM Solutions
Competitive Environment—Global PAM Solutions
Revenue Share by Verticals—Global PAM Solutions
Revenue Share by Horizontals—Global PAM Solutions
Revenue Share by Top Participants—Global PAM Solutions
Key Growth Metrics for PAM Solutions—North America
Revenue Forecast for PAM Solutions—North America
Revenue Forecast by Product for PAM Solutions—North America
Revenue Forecast Analysis for PAM Solutions—North America
Key Growth Metrics for PAM Solutions—EMEA
Revenue Forecast for PAM Solutions, EMEA
Revenue Forecast by Product for PAM Solutions—EMEA
Revenue Forecast Analysis for PAM Solutions—EMEA
Key Growth Metrics for PAM Solutions—LATAM
Revenue Forecast for PAM Solutions—LATAM
Revenue Forecast by Product for PAM Solutions—LATAM
Revenue Forecast Analysis for PAM Solutions—LATAM
Key Growth Metrics for PAM Solutions—Asia-Pacific
Revenue Forecast for PAM Solutions—Asia-Pacific
Revenue Forecast by Product for PAM Solutions—Asia-Pacific
Revenue Forecast Analysis for PAM Solutions—Asia-Pacific
Growth Opportunity 1: Growing Demand for PAM to Secure Cloud and OT Environments
Growth Opportunity 1: Growing Demand for PAM to Secure Cloud and OT Environments (continued)
Growth Opportunity 2: Centralized PAM Management for On-premises, Hybrid, or Multi-cloud Environments
Growth Opportunity 2: Centralized PAM Management for On-premises, Hybrid, or Multi-cloud Environments (continued)
Growth Opportunity 3: Integration of PAM With Other Security Technologies for a More Holistic Security Strategy
Growth Opportunity 3: Integration of PAM With Other Technologies for a More Holistic Security Strategy (continued)
Your Next Steps
Why Frost, Why Now?
List of Exhibits
List of Exhibits (continued)
Legal Disclaimer
Popular Topics
| No Index | No |
|---|---|
| Podcast | No |
| Author | Vivien Pua |
| Industries | Information Technology |
| WIP Number | PC4D-01-00-00-00 |
| Is Prebook | No |
| GPS Codes | 9659 |
 USD
USD GBP
GBP CNY
CNY EUR
EUR INR
INR JPY
JPY MYR
MYR ZAR
ZAR KRW
KRW THB
THB




